Astah - How wonderful you are!
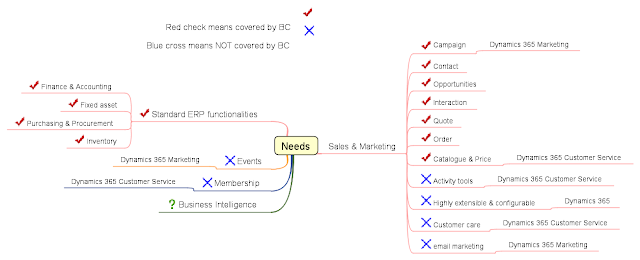
I started using JUDE in the early days of UML modelling and have continued using Astah until now. In the day and age of Agile development, emphasizing "communication over documentation", is UML (and related UML tools) still relevant? I'll give a resounding YES! to the question. While we should do away with extensive documentation , we should still be able to communicate our intent in forms of architecture, design, workflow, processes, etc. In the course of my work in an end-user environment, I use Astah extensively to communicate with development teams, users, vendors and even senior management. I find it's often a lot easier to use a tool like Astah to draw UML (or pseudo-UML) diagrams than pen-and-paper (or even napkins!). For instance, I can easily move things around, redraw and append/ update the diagram using the tool but not with paper. Some examples of diagrams I'd used in the course of work are below. I used Astah for the following: Share my thought proc...





