Cookie, Security, OWASP
We just had a Security Assessment for our web applications. Some points of interest follows:
Cookie
- XSS security: Where possible, all cookies should be configured to be httpOnly. This is to prevent client-side scripts or applets from accessing the cookie. Incidentally, this is the default for ASP.NET session cookie and cannot be changed via httpCookies element in Web.Config: <httpCookies httpOnlyCookies="true"/>
- Prevent MITM from accessing the session: Ensure that the session cookie is delivered over secured HTTP session (TLS). Setting the cookie as secured indicates to the browser that the cookie should only be sent over a secured channel. To configure the httpCookies element: <httpCookies requireSSL="true" />
- Note that Forms and Session cookies have slightly different behaviour with Forms cookie being more secured and more configurable.
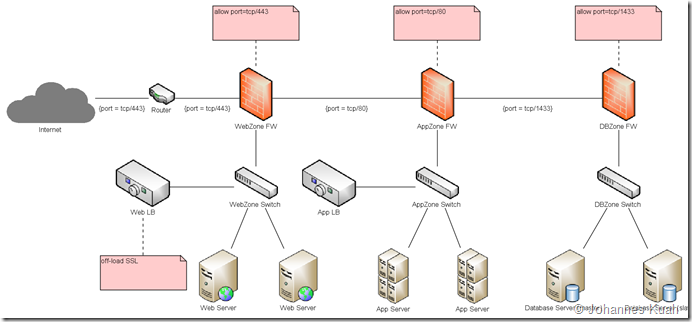
- Interestingly, setting requireSSL to true for Forms cookie mandates that the communication channel to the web server be secured whereas Session cookie does not. This scenario applies in cases where the SSL terminates at the load balancers (LB) and the channel between the LB and the web server isn’t secured.
- GA sets several persistent cookies by default. The cookies are well examined here. Although the cookies appears to be issued from the same domain (1st party cookie), modifying the httpCookies element (httpOnlyCookies, requireSSL) does not appear to affect GA’s cookies.
IIS Server
- IIS is susceptible to HTTP 1.0 attacks whereby a HTTP 1.0 request without the host header would cause IIS to leak the IP address of the host.
- This issue has been discussed here.

Comments